I have recently been configuring Network Access Control with 802.1x, and I had been having issues with using multiple RADIUS servers on Ruckus ICX Switches. The main issue being:
RADIUS Authenticate over SSH to switch using Microsoft NPS RADIUS Server
RADIUS Authenticate using 802.1x or MAC-Auth using DOT1x RADIUS Server
In Ruckus ICX switches there isn’t any concept of AAA groups like in Cisco, where you can designate specific RADIUS traffic to go to various different RADIUS Servers.
I have found 2 work arounds, I did however also call support and spend 1 hour troubleshooting with them and they didn’t have an answer for me.
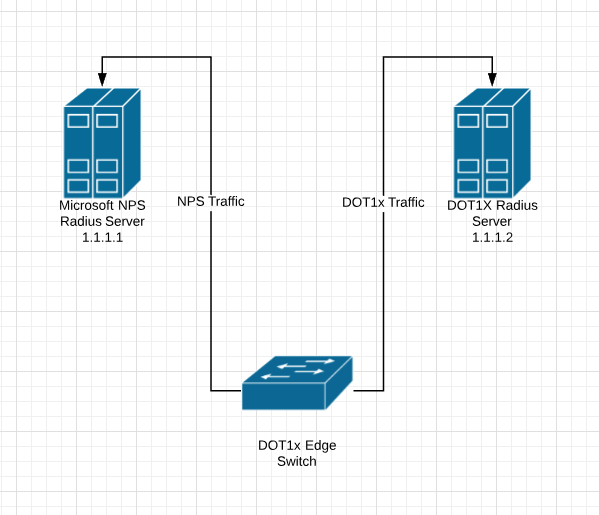
Some Basic Setup Information
Microsoft NPS RADIUS Server : 1.1.1.1
DOT1x RADIUS Server : 1.1.1.2
Here are my AAA Authentication Commands:
SSH@tpw-sw1# sh run | inc authentication aaa authentication web-server default radius local aaa authentication enable default radius local aaa authentication dot1x default radius aaa authentication login default radius local
Here are my 2 work arounds:
WORKAROUND 1
SSH@tpw-sw1(config)# radius-server host 1.1.1.1 auth-port 1812 acct-port 1813 default key RADIUS1SECRET SSH@tpw-sw1(config)# radius-server host 1.1.1.2 auth-port 1812 acct-port 1813 default key RADIUS2SECRET dot1x mac-auth
If you use the 1.1.1.2 RADIUS server first in the list you cannot authenticate to the switch at all, even over super-user-password. So the only way I have it working is to have the DOT1x Radius Server listed 2nd but calling out DOT1x and MAC-AUTH.
WORKAROUND 2
The other method I found is to apply a command at the interface level:
SSH@tpw-sw1# conf t SSH@tpw-sw1(config)# int ethernet 1/1/1 SSH@tandy-lab-sw1(config-if-e1000-1/1/1)#use-radius-server 1.1.1.2
I hope that this helps, I spent a day trying to figure it out 🙂

